Undergraduate experience

Critical infrastructure includes our nation’s transportation, commerce channels, energy and clean drinking water and all the systems that support the continued running of these networks. To encourage students to start thinking about important issues facing homeland security, CAOE organized a student challenge event in February 2022 in partnership with four DHS Centers of Excellence.
This event was the third hackathon event organized by CAOE and the first event with participation from multiple DHS Centers of Excellence including Critical Infrastructure Resilience Institute (CIRI) – Criminal Investigations and Network Analysis Center (CINA); Maritime Security Center (MSC) and National Counterterrorism Innovation, Technology and Education (NCITE). Each COE contributed to the planning of the event and had students from their home universities and partner institutions participate in the challenge.
The three-day hybrid event paired students with academic, DHS and industry mentors to focus on mitigation strategies to combat emerging threats to the nation’s critical infrastructure, such as protecting against cyberattacks on the food distribution network.
The event was kicked off by Bob Kolasky, Director, U.S. DHS Cybersecurity and Infrastructure Security Agency (CISA)\ National Risk Management Center (NRMC)/ Kolasky articulated the NRMC’s critical focus on staying ahead of evolving cyber and physical threats and its dependence on a unified effort through collaboration. “Something that’s really important in the area of critical infrastructure is information sharing and having the ability to work across government through industry, through different levels of government in collaboration with industry, to share information, particularly about cyberthreats and cyber vulnerabilities.” There’s so much that goes on in almost near real-time, and we are trying to collect that information an understanding of how things playing out in cyberspace or in a supply chain that could have downstream the impacts on the effect of infrastructure, and how we can share that information so that they can be used by network defenders,” explained Kolasky.
Dr. Stephen Flynn, Founding Director Global Resilience Center (GRI) at Northeastern University and Professor of Political and an internationally renowned expert in critical infrastructure and supply chain security and resilience, shared his expertise to give the students real-world context to the challenge scenarios explaining possible attack scenarios, adversarial actors, risk, vulnerabilities, security gaps, policy, foundational knowledge, and countermeasure strategies. Flynn closed by explaining “ It really is fundamentally about looking to understand key systems, and then digging deep into them, to understand where vulnerabilities and where consequences might accrue from them, and developing strategies ideally to mitigate those risk of cascading factors. [Systems] will fail at some point, so have good plans for recovery and don’t just put them back the way they were before, because they probably were not good enough. Adapt them, make them better, and then we’ll be in a much better place”
Gregory Simmons, Program Manager for Minority Serving Institutions and Workforce Development, Office of University Programs, DHS S&T shared information on career paths, internship opportunities and workforce development tracks for public service. He mentioned, “ the average age of homeland security professionals is over 50 and there is a real need to recruit younger innovative talent not just as government employees but throughout the homeland security enterprise including industry”
Sixteen teams including 73 students from multiple universities competed in solving possible real-world threats to critical infrastructure with a winning team selected for each of the proposed scenarios.
Winning Teams and Proposed Solutions
Problem Statement 1
How can we support the United States infrastructure to detect when an autonomous vehicle has been hijacked or had its system taken over?
SIT Takes on Problem Statement 1
Stevens Institute of Technology: Christopher Francis and Daniel Kadyrov
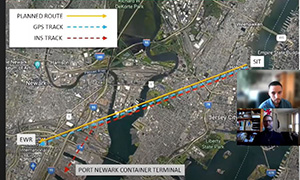
INS Systems and Domain Awareness Communication Protocols to Facilitate Hijack Detection
This solution looks to prevent bad actors from using a “spoofed” GPS signal from tricking an autonomous vehicle into taking an unapproved path. To mitigate GPS “spoofing” their resolution focused on implementing real-time joint broadcast protocols employing a GPS track coupled with an Inertial Navigation System (INS).
Problem Statement 2
How can we support identification of the rising tide of illegal activity even on open source networks while protecting our nation’s critical infrastructure?
Fulcrum
Arizona State University: Taylor Foster; Rishik Kolli; Siddhant Labade; Vanesh Mani; Naveen Ramesh; Logan Van Pelt
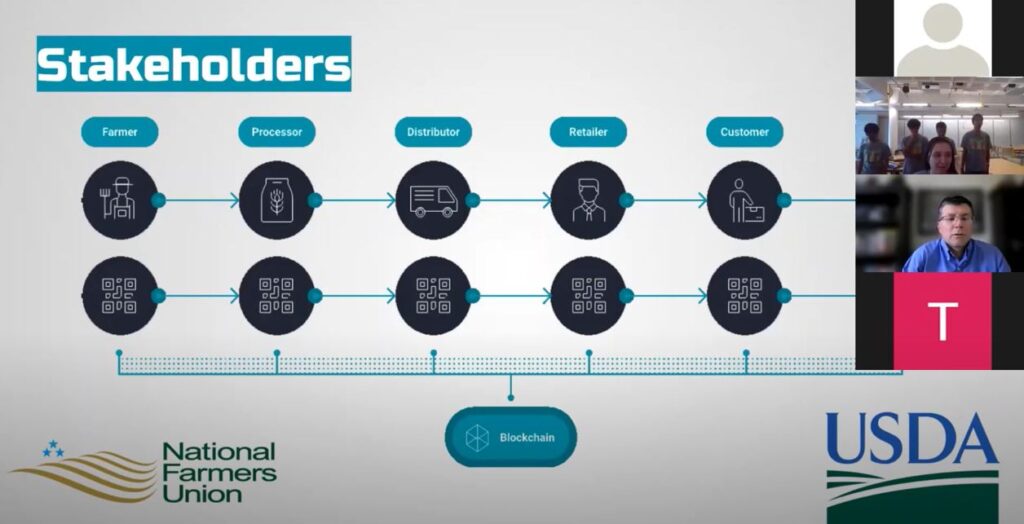
Blockchain and Asymmetric Encryption to Agricultural Supply Chain
This solution is aiming to prevent illegal activity, specifically food fraud by tracking it at all steps of the supply chain. The team suggests using blockchain technology to keep a shared ledger across all food distributors so that there is verifiable data about where food has come from and what treatments it has gone under. Their proposed solution focused on an open-source blockchain application for the global agricultural industry in collaboration with FDA and USDA public-private partnership programs
Problem statement 3
How might we mitigate attacks on digital elements of our nation’s critical infrastructure through prevention, and/or response?
Winning Team
CINA Team 7
George Mason University: Hajar Al-Ali; Casey Cho; Husnain Choudhry; Amaha Isayas; Junaid Naick
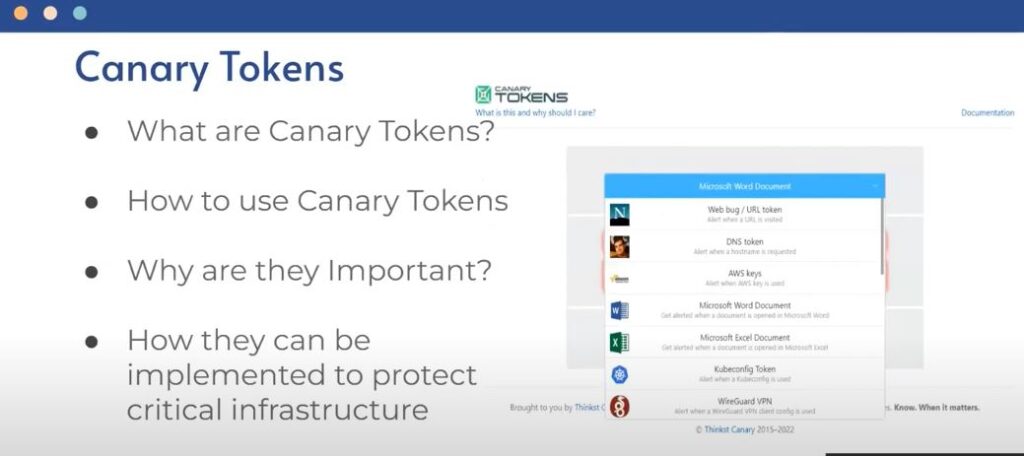
Integrating Tool for Active Defense in Critical Infrastructure
Their solution focused on cyber resilience and addressed security gaps in lower-level cyber security environments. To prevent attacks similar to that on the water treatment plant in Oldsmar, FL, the team suggested a suite of security protocols that even small towns with potentially low budgets could use. Their multi-tiered solution involved the application of security dashboards, honey users/honey pots, canary tokens and port spoofing techniques
Honorable Mention
L33TCOD3R5
A combined team from Stevens Institute of Technology: Liam Brew; Michael Bearint; Andrew Navarez; Ryan Potenza; Jason Wong; and Tricia Camaya of Northeastern University.
Asset-Focused Security
This solution proposes preventing attacks rather than reacting to them by having regular risk assessment reports done and, using the data from those reports to determine which assets are most vulnerable and focusing security measures on those assets. The proactive risk-management premise is designed to reduce compromises and provide strategies for reacting and responding through the use of database implementation, machine learning improvements and predictive measures to improve cybersecurity posture.
